Information Technology Services
Reliable, fast & tuned Computer Personally for you.
+
Asset Protected
+
Client Trust Us
+
Our Industries
Comprehensive Turnkey Computers
We specialize in providing fully configured computers instantaneously available for operation, ensuring a seamless experience from acquisition to implementation. Our expert guidance helps you understand your options, optimize costs, and acquire the most suitable computing resources to address your needs while meeting contemporary standards.
Don't Waste Time
Risk Assessment and Management
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
- Easy Subscribtion Package
- Secure Payment Method
” Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis “
Database Security
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
Server Administrator
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
Global Cyber Security
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
Authorized partner of Premium Software
As authorized partners of premium software, including offerings from industry leaders such as Microsoft, Avast, Eset, and Adguard, we guarantee the authenticity and reliability of our products, ensuring optimal performance and security for your systems.
IT Mastery With Our Expert Services
We offer top-notch IT services. Our expertise ensures smooth solutions, pushing your business ahead in the digital world.
Equipment prevention.
Carrying out regular hardware maintenance will allow you to maintain your computer in working order and avoid problems associated with slowing down or stopping its operation.
Installing the operating system
This procedure brings the computer to its best state when malware infected it or after many program installs and uninstalls. Reinstalling the OS restores peak reliability and speed.
Removing malware
Carrying out an anti-virus scan of the computer file system using two and more different antivirus scanners. It is a good practice to thoroughly check your computer's file system for any malware or viruses.
Tuning and customization
Tuning and configuration will allow you to achieve the maximum from your computer productivity by tailoring your system to meet your specific needs and requirements seamlessly.
Recovering lost data
Sometimes it happens that users lose photos, documents, important files or other valuable data. They could have been removed inadvertently or damaged. malware. We will help you recover this data.
Setting up networks
We will help you set up a local network between computers at home or in the office. Set up general Internet connection. Optimize your wireless WiFi connection. Tune corporate email and other network services.

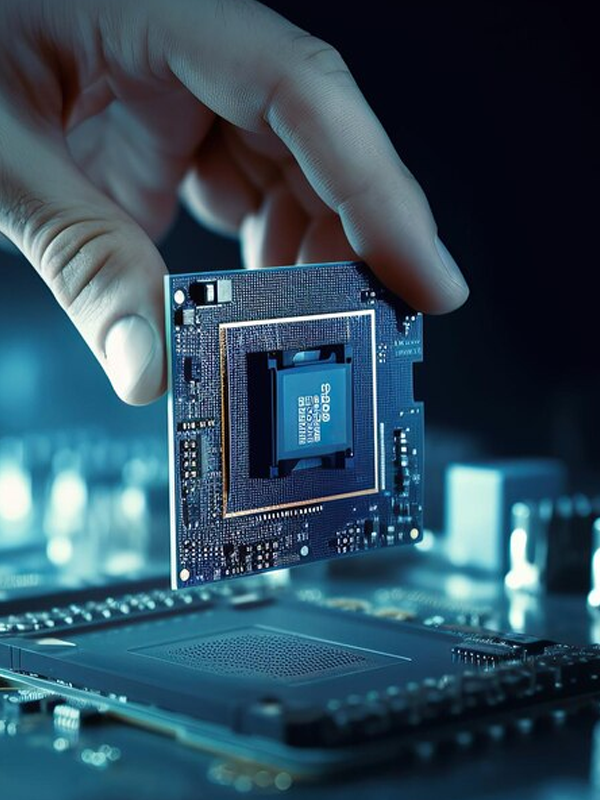
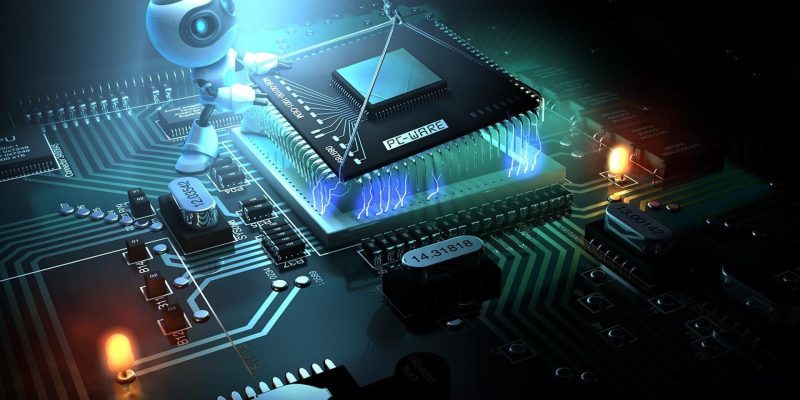
Tailored services propel business by meeting unique needs. Solutions enhance efficiency, foster growth, and ensure organizations stay ahead through technology, consulting, and leveraging advances—paving sustained success.
- We will help you choose the optimal configuration for your future computer in accordance with the tasks it will need to solve. You won't have to overpay for redundant features that you will never use.
- We'll help choose the best antivirus based on independent lab tests. Criteria includes malware detection, performance, ease of use, and extra features. Labs regularly test top antivirus makers.
- The entire range of products from one of the leading manufacturers of computer equipment, Lenovo

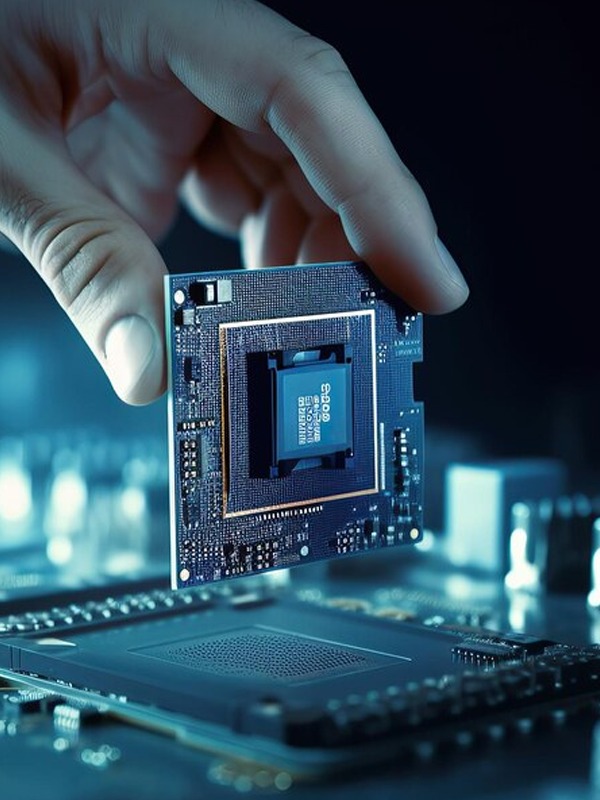
Tailored services propel business by meeting unique needs. Solutions enhance efficiency, foster growth, and ensure organizations stay ahead through technology, consulting, and leveraging advances—paving sustained success.
Turnkey Computer
We will help you choose the optimal configuration for your future computer in accordance with the tasks it will need to solve. You won't have to overpay for redundant features that you will never use.
Protection Of Data And Software
We'll help choose the best antivirus based on independent lab tests. Criteria includes malware detection, performance, ease of use, and extra features. Labs regularly test top antivirus makers.
Leading Lenovo Products
The entire range of products from one of the leading manufacturers of computer equipment, Lenovo
How Its Work
Easy Step offer a range of cybersecurity services
01
Talk With Us
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
02
Contract Created
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
03
Happy Secure Work
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
Our Business Number
Ensure your cloud services are secure with our cloud security services
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Threats Protection
Lorem ipsum dolor sit amet
Protected Guarantee
Lorem ipsum dolor sit amet


4.8 Ratings Feedback
Based From Google Listing
Our Pricing
Choose Our Pricing Plans Recomendation
learn more about our cybersecurity services and schedule a free consultation.
Booking Schedule
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
legal Activity
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Range Consultation
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Discover firsthand experiences from clients who have partnered with us on their journey to digital excellence.


